Data security and compliance in remote patient monitoring (RPM) is critical. As RPM grows quickly in the U.S., so do data breaches, exposing sensitive health data and affecting millions of patients and clinics.
- In 2023, more than 133 million healthcare records were breached in the U.S. (HIPAA Journal).
- Each incident cost providers an average of $10.93 million, the highest of any industry (IBM).
A data breach means patients lose privacy and risk misuse of their health data, while clinics face lawsuits, HIPAA fines of up to $1.5 million per year, and damaged trust.
That’s why it’s important to understand data security and compliance in RPM. In this blog, you’ll learn what data security and compliance means in RPM, which rules apply, how clinics can protect data and the risks of ignoring compliance.
Sources: Healthcare Data Breach Statistics
Data Security and Compliance in RPM: Key Takeaways
Data security in RPM means protecting patient information at every stage: device, transfer, storage, and access.
Compliance rules matter: HIPAA safeguards privacy, HITECH enforces accountability, and CMS ensures billing is accurate and secure.
Practical safeguards like encryption, role-based access, HIPAA-compliant storage, audit trails, and secure devices keep data safe in daily operations.
Ignoring compliance is costly: Patients lose trust, while clinics face HIPAA fines, lawsuits, failed CMS audits, and long-term reputation damage.
Best practices build trust: Staff training, compliant vendors, strong audit processes, and open communication with patients make compliance part of everyday care.
The future of RPM security will bring AI-driven monitoring, blockchain-based recordkeeping, and stricter rules from regulators.
Data Security and Compliance in Remote Patient Monitoring
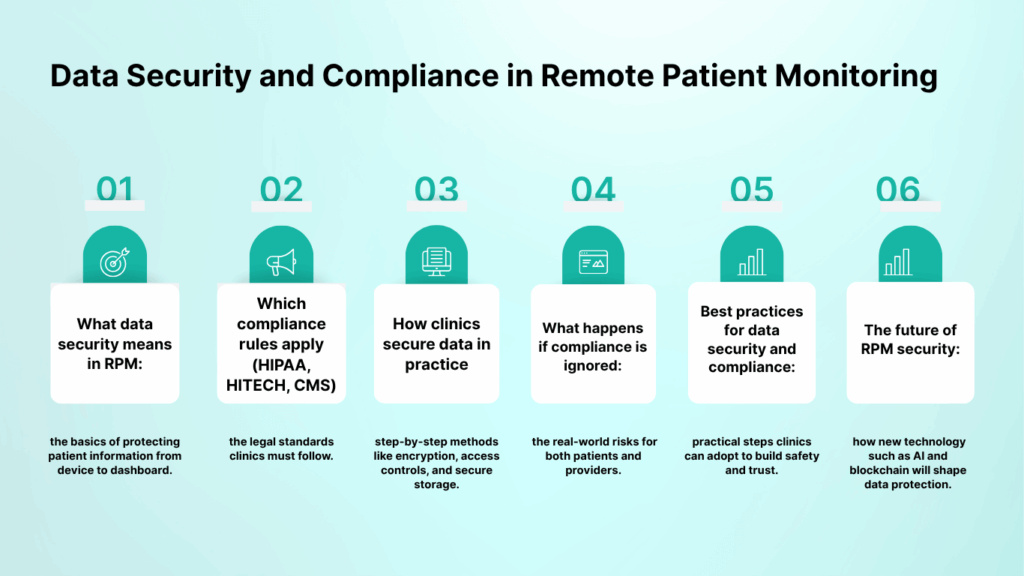
We’ve seen why security and compliance are critical. To answer this question clearly, let’s break it down into smaller parts. In this blog, we will explain:
- What data security means in RPM: the basics of protecting patient information from device to dashboard.
- Which compliance rules apply (HIPAA, HITECH, CMS): the legal standards clinics must follow.
- How clinics secure data in practice: step-by-step methods like encryption, access controls, and secure storage.
- What happens if compliance is ignored: the real-world risks for both patients and providers.
- Best practices for data security and compliance: practical steps clinics can adopt to build safety and trust.
- The future of RPM security: how new technology such as AI and blockchain will shape data protection.
This roadmap gives a clear path for understanding not only what the rules are, but also how they work in practice and why they matter for both patients and clinics.
What does data security mean in remote patient monitoring (RPM)?
In remote patient monitoring, data security means protecting every piece of health information a patient shares through connected devices. This protection starts the moment a reading is taken at home and continues until it reaches the provider’s system.
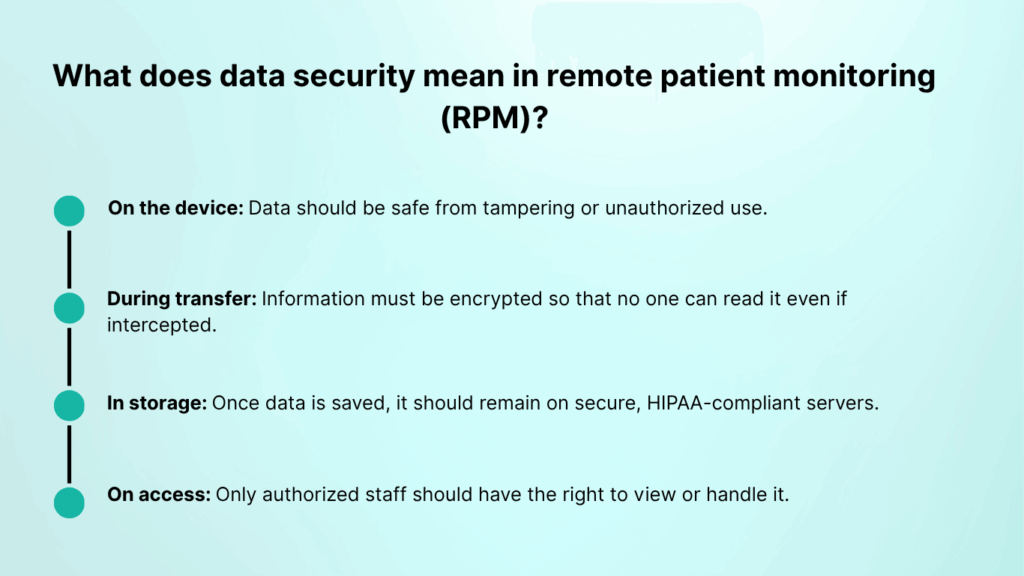
RPM devices capture sensitive details such as blood pressure, glucose levels, or heart rate. These are classified as protected health information (PHI) under HIPAA. To make this easier to understand, think of patient data as moving through four main stages:
- On the device: Data should be safe from tampering or unauthorized use.
- During transfer: Information must be encrypted so that no one can read it even if intercepted.
- In storage: Once data is saved, it should remain on secure, HIPAA-compliant servers.
- On access: Only authorized staff should have the right to view or handle it.
These steps connect together like links in a chain. If even one link breaks, patient information can be exposed. That is why security in RPM is not a single action but a process that protects data at every stage.
Which compliance rules apply to RPM? (HIPAA, HITECH, CMS)
Data security in remote patient monitoring is a legal requirement. In the United States, three main sets of rules guide how clinics must handle patient data and billing.
1. HIPAA (Health Insurance Portability and Accountability Act)
HIPAA is the foundation of healthcare privacy. It requires encryption, access limits, and proper staff training to protect protected health information (PHI). In RPM, this covers every reading from a blood pressure cuff or glucose meter that travels to a provider’s dashboard.
A single breach can lead to fines of up to 50,000 dollars per violation, with annual penalties as high as 1.5 million dollars.
2. HITECH Act (Health Information Technology for Economic and Clinical Health)
The HITECH Act strengthened HIPAA by making breach reporting mandatory and raising penalties for negligence. For RPM, this means clinics cannot hide a data loss. If devices or platforms fail and PHI is exposed, the event must be reported, and the clinic is held accountable.
3. CMS (Centers for Medicare & Medicaid Services) Compliance
CMS rules apply when clinics bill RPM services to Medicare. They require providers to:
- Use the correct CPT codes (99453, 99454, 99457, 99458)
- Keep accurate records that prove time and services delivered
- Store billing data securely for audits
In practice, this means a clinic must prove to CMS that it monitors data safely, documents it properly, and bills patients only for verified services.
Together, these rules protect patient privacy while ensuring clinics are transparent and accountable. Ignoring them can lead to fines, failed audits, and loss of patient trust.
How Do Clinics Secure Data in Remote Patient Monitoring?
Compliance rules such as HIPAA and CMS define the standards, but clinics also need to apply practical steps every day to keep data safe. In remote patient monitoring, security covers the entire journey of information from the device to the provider’s dashboard.
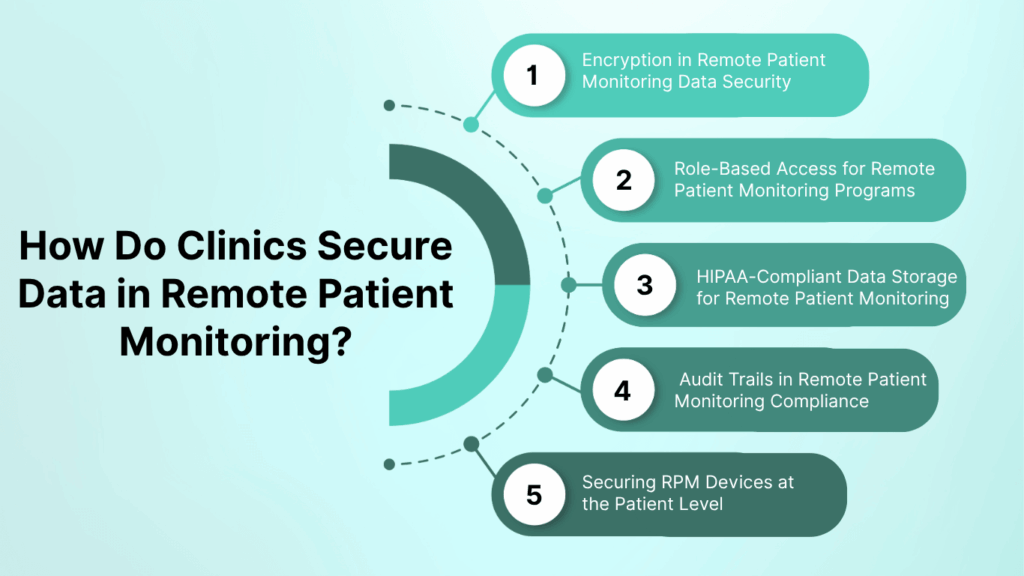
1. Encryption in Remote Patient Monitoring Data Security
Encryption protects patient data when it leaves the device, while it travels online, and when it is stored. Even if someone intercepts the information, encryption ensures it cannot be read or misused. This is the first layer of protection in any RPM program.
2. Role-Based Access for Remote Patient Monitoring Programs
Not every staff member needs the same level of access. Role-based access limits sensitive information to only those who need it, such as doctors, nurses, or administrators. This prevents accidental exposure and reduces the risk of internal misuse.
3. HIPAA-Compliant Data Storage for Remote Patient Monitoring
All RPM data must be stored on secure, HIPAA-compliant servers. Many clinics use trusted cloud platforms that meet healthcare standards and provide redundancy. This ensures that patient readings are safe, backed up, and available only through secure channels.
4. Audit Trails in Remote Patient Monitoring Compliance
Audit trails track every access and action taken with patient information. If a record is opened or changed, the system logs who did it and when. This helps clinics detect unusual activity and also provides proof of compliance during audits.
5. Securing RPM Devices at the Patient Level
Security begins at the patient’s home. Pre-configured RPM devices, especially those with built-in cellular connections, reduce risks compared to Wi-Fi devices. They are easier for patients to use and less vulnerable to weak home internet security.
Together, these measures build a system where data stays protected from start to finish. More importantly, they show both regulators and patients that a clinic treats sensitive health information with the seriousness it deserves.
When clinics ignore security safeguards or fail to meet compliance standards, the risks fall on both patients and providers. The results can be damaging and long-lasting.
Patient Risks in Remote Patient Monitoring Data Breaches
The biggest consequence is the loss of privacy. A single data breach can expose personal health details, and in some cases, that information ends up misused for identity theft or sold on the black market. Beyond the technical risks, patients often lose confidence in their providers. If they feel their information isn’t safe, many will refuse to participate in RPM programs, which limits the success of remote care.
Provider Risks in Remote Patient Monitoring Non-Compliance
The impact is just as serious.
- HIPAA penalties can reach 50,000 dollars per violation, with yearly totals up to 1.5 million dollars.
- CMS audits may reject claims or demand repayment if records are incomplete or mishandled.
- Legal exposure grows as patients affected by breaches file lawsuits.
- Reputation damage lingers long after the event, making it difficult to regain trust and re-enroll patients in RPM services.
A single weak point in security can undo years of progress. Instead of improving care and building trust, RPM becomes a liability that drains resources and harms both sides.
The Future of Data Security and Compliance in Remote Patient Monitoring
As RPM adoption grows, data security requirements will continue to evolve. Clinics that plan ahead will be better prepared for stricter rules and new technologies that shape how patient information is protected.
1. Smarter detection with AI
Artificial intelligence is being used to monitor unusual patterns in data access. For example, if someone logs in at an odd time or downloads large amounts of information, AI can raise alerts before damage is done. This kind of proactive monitoring will become standard in RPM platforms.
2. Blockchain for health records
Blockchain technology offers a way to create tamper-proof logs of patient data. Each action is recorded in a secure, traceable way, which can make it easier for clinics to prove compliance during audits and reassure patients that their records cannot be altered.
3. Stricter rules from regulators
As the use of RPM expands, HIPAA and CMS guidelines may be updated to address new risks. Clinics should expect more detailed requirements for device security, reporting standards, and patient consent. Preparing now will make it easier to stay ahead of future changes.
Final Thoughts
Remote patient monitoring has the power to improve care, but it only works if patients and clinics can trust that sensitive health data is protected. Security and compliance are the foundation of a successful RPM program.
The message is simple: protecting data in remote patient monitoring is about more than avoiding penalties. It is about respecting patient privacy, meeting legal obligations, and building programs that patients and providers can rely on.
Clinics that make security and compliance a priority today will be better prepared for the future of digital healthcare.
Frequently Asked Questions (FAQs)
What is data security in remote patient monitoring?
Data security in remote patient monitoring means protecting all health information collected by devices at home, such as blood pressure or glucose readings. Security covers every stage, from the device, during transfer, in storage, and when staff access it, to keep data safe from breaches or misuse.
How do you ensure data security and compliance?
Clinics ensure data security and compliance by following HIPAA and CMS rules. This includes encrypting patient information, limiting access to authorized staff, storing data on HIPAA-compliant servers, keeping audit logs, training employees, and working with secure vendors.
What are the requirements for remote patient monitoring?
The main requirements for remote patient monitoring are:
- Patients must have a qualifying medical need (such as hypertension or diabetes).
- Providers must use FDA-approved or clinically validated devices.
- Data must be collected and transmitted securely.
- Clinics must follow HIPAA and HITECH for privacy.
- Medicare billing requires use of CPT codes like 99453, 99454, 99457, and 99458.
What type of data can be collected through remote patient monitoring?
RPM devices can collect different types of health data, depending on the patient’s condition. Common examples include:
- Blood pressure readings
- Blood glucose levels
- Heart rate and rhythm
- Weight and oxygen saturation
- Activity and sleep patterns
All of this information is considered protected health information (PHI) and must be secured under HIPAA.